- Introduction to the ASA
- Getting Started
- Managing Feature Licenses
- Configuring the Transparent or Routed Firewall
- Configuring Multiple Context Mode
- Starting Interface Configuration (ASA 5510 and Higher)
- Starting Interface Configuration (ASA 5505)
- Completing Interface Configuration (Routed Mode)
- Completing Interface Configuration (Transparent Mode)
- Configuring the Hostname, Domain Name, Passwords, and Other Basic Settings
- Configuring DHCP
- Configuring Dynamic DNS
- Adding Global Objects
- Information About Access Lists
- Adding an Extended Access List
- Adding an EtherType Access List
- Adding a Standard Access List
- Adding a Webtype Access List
- Adding an IPv6 Access List
- Configuring Logging for Access Lists
- Information About Routing
- Configuring Static and Default Routes
- Defining Route Maps
- Configuring OSPF
- Configuring RIP
- Configuring EIGRP
- Configuring Multicast Routing
- Configuring IPv6 Neighbor Discovery
- Information About NAT
- Configuring Network Object NAT
- Configuring Twice NAT
- Configuring a Service Policy
- Configuring Special Actions for Application Inspections (Inspection Policy Map)
- Configuring Access Rules
- Configuring AAA Servers and the Local Database
- Configuring the Identity Firewall
- Configuring AAA for Network Access
- Configuring Management Access
- Configuring Filtering Services
- Configuring Web Cache Services Using WCCP
- Configuring Digital Certificates
- Getting Started With Application Layer Protocol Inspection
- Configuring Inspection of Basic Internet Protocols
- Configuring Inspection of Voice and Video Protocols
- Configuring Inspection of Database and Directory Protocols
- Configuring Inspection of Management Application Protocols
- Information About Cisco Unified Communications Features
- Configuring the Cisco Phone Proxy
- Configuring the TLS Proxy for Encrypted Voice Inspection
- Configuring Cisco Mobility Advantage
- Configuring Cisco Unified Presence
- Configuring Cisco Unified Communications Intercompany Media Engine
- Configuring Connection Limits and Timeouts
- Configuring QoS
- Configuring the Botnet Traffic Filter
- Configuring Threat Detection
- Using Protection Tools
- Configuring the IPS Module
- Configuring the ASA CX Module
- Configuring the Content Security and Control Application on the CSC SSM
- Information About High Availability
- Configuring Active/Standby Failover
- Configuring Active/Active Failover
- Configuring IPSec and ISAKMP
- Configuring L2TP over IPSec
- Setting General VPN Parameters
- Configuring Tunnel Groups, Group Policies, and Users
- Configuring IP Addresses for VPN
- Configuring Remote Access VPNs
- Configuring Network Admission Control
- Configuring Easy VPN on the ASA 5505
- Configuring the PPPoE Client
- Configuring LAN-to-LAN VPNs
- Configuring Clientless SSL VPN
- Configuring AnyConnect VPN Client Connections
- Configuring AnyConnect Host Scan
- Configuring Logging
- Configuring Network Secure Event Logging (NSEL)
- Configuring SNMP
- Configuring Smart Call-Home
- Managing Software and Configurations
- Troubleshooting
- Using the Command-Line Interface
- Addresses, Protocols, and Ports
- Configuring an External Server for Security Appliance User Authorization
Results
Updated: September 24, 2007Chapter: Configuring the Transparent or Routed Firewall
Chapter Contents- Information About the Firewall Mode
- Information About Routed Firewall Mode
- Information About Transparent Firewall Mode
- Using the Transparent Firewall in Your Network
- Bridge Groups
- Management Interface (ASA 5510 and Higher)
- Allowing Layer 3 Traffic
- Allowed MAC Addresses
- Passing Traffic Not Allowed in Routed Mode
- Passing Traffic For Routed-Mode Features
- BPDU Handling
- MAC Address vs. Route Lookups
- ARP Inspection
- MAC Address Table
- Task Flow for Configuring ARP Inspection
- Adding a Static ARP Entry
- Enabling ARP Inspection
- Adding a Static MAC Address
- Disabling MAC Address Learning
- Monitoring ARP Inspection
- Monitoring the MAC Address Table
- How Data Moves Through the ASA in Routed Firewall Mode
- An Inside User Visits a Web Server
- An Outside User Visits a Web Server on the DMZ
- An Inside User Visits a Web Server on the DMZ
- An Outside User Attempts to Access an Inside Host
- A DMZ User Attempts to Access an Inside Host
- An Inside User Visits a Web Server
- An Inside User Visits a Web Server Using NAT
- An Outside User Visits a Web Server on the Inside Network
- An Outside User Attempts to Access an Inside Host
Configuring the Transparent or Ro uted Fir ewall
- Information About the Firewall Mode
- Licensing Requirements for the Firewall Mode
- Default Settings
- Guidelines and Limitations
- Setting the Firewall Mode
- Configuring ARP Inspection for the Transparent Firewall
- Customizing the MAC Address Table for the Transparent Firewall
- Monitoring the Transparent Firewall
- Firewall Mode Examples
- Feature History for the Firewall Mode
Information About the Firewall Mode
- Information About Routed Firewall Mode
- Information About Transparent Firewall Mode
Information About Routed Firewall Mode
In routed mode, the ASA is considered to be a router hop in the network. Routed mode supports many interfaces. Each interface is on a different subnet. You can share interfaces between contexts.
The ASA acts as a router between connected networks, and each interface requires an IP address on a different subnet. The ASA supports multiple dynamic routing protocols. However, we recommend using the advanced routing capabilities of the upstream and downstream routers instead of relying on the ASA for extensive routing needs.
Information About Transparent Firewall Mode
Traditionally, a firewall is a routed hop and acts as a default gateway for hosts that connect to one of its screened subnets. A transparent firewall, on the other hand, is a L ayer 2 firewall that acts like a “bump in the wire,” or a “ stealth firewall,” and is not seen as a router hop to connected devices.
- Using the Transparent Firewall in Your Network
- Bridge Groups
- Management Interface (ASA 5510 and Higher)
- Allowing Layer 3 Traffic
- Allowed MAC Addresses
- Passing Traffic Not Allowed in Routed Mode
- BPDU Handling
- MAC Address vs. Route Lookups
- ARP Inspection
- MAC Address Table
Using the Transparent Firewall in Your Network
The ASA connects the same network between its interfaces. Because the firewall is not a routed hop, you can easily introduce a transparent firewall into an existing network.
Figure 5-1 shows a typical transparent firewall network where the outside devices are on the same subnet as the inside devices. The inside router and hosts appear to be directly connected to the outside router.
Figure 5-1 Transparent Firewall Network
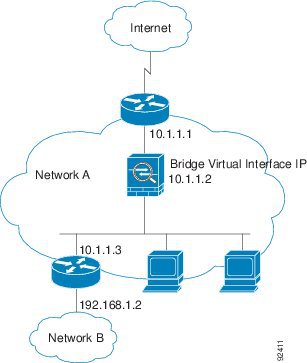
Bridge Groups
If you do not want the overhead of security contexts, or want to maximize your use of security contexts, you can group interfaces together in a bridge group, and then configure multiple bridge groups, one for each network. Bridge group traffic is isolated from other bridge groups; traffic is not routed to another bridge group within the ASA, and traffic must exit the ASA before it is routed by an external router back to another bridge group in the ASA. Although the bridging functions are separate for each bridge group, many other functions are shared between all bridge groups. For example, all bridge groups share a syslog server or AAA server configuration. For complete security policy separation, use security contexts with one bridge group in each context.
Figure 5-2 shows two networks connected to the ASA, which has two bridge groups.
Figure 5-2 Transparent Firewall Network with Two Bridge Groups
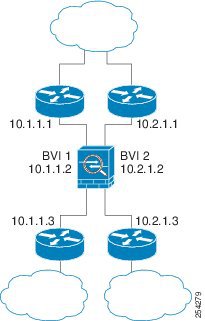
Note Each bridge group requires a management IP address. The ASA uses this IP address as the source address for packets originating from the bridge group. The management IP address must be on the same subnet as the connected network. For another method of management, see the “Management Interface (ASA 5510 and Higher)” section.
The ASA does not support traffic on secondary networks; only traffic on the same network as the management IP address is supported.
Management Interface (ASA 5510 and Higher)
In addition to each bridge group management IP address, you can add a separate Management slot / port interface that is not part of any bridge group, and that allows only management traffic to the ASA. For more information, see the “Management Interface” section.
Allowing Layer 3 Traffic
- Unicast IPv4 and IPv6 traffic is allowed through the transparent firewall automatically from a higher security interface to a lower security interface, without an ACL.
Note Broadcast and multicast traffic can be passed using access rules. See the “Allowing Broadcast and Multicast Traffic through the Transparent Firewall Using Access Rules” section for more information.
- ARPs are allowed through the transparent firewall in both directions without an access list. ARP traffic can be controlled by ARP inspection.
- For Layer 3 traffic travelling from a low to a high security interface, an extended access list is required on the low security interface. See “Adding an Extended Access Control List,” for more information.
Allowed MAC Addresses
The following destination MAC addresses are allowed through the transparent firewall. Any MAC address not on this list is dropped.
- TRUE broadcast destination MAC address equal to FFFF.FFFF.FFFF
- IPv4 multicast MAC addresses from 0100.5E00.0000 to 0100.5EFE.FFFF
- IPv6 multicast MAC addresses from 3333.0000.0000 to 3333.FFFF.FFFF
- BPDU multicast address equal to 0100.0CCC.CCCD
- AppleTalk multicast MAC addresses from 0900.0700.0000 to 0900.07FF.FFFF
Passing Traffic Not Allowed in Routed Mode
In routed mode, some types of traffic cannot pass through the ASA even if you allow it in an access list. The transparent firewall, however, can allow almost any traffic through using either an extended access list (for IP traffic) or an EtherType access list (for non-IP traffic).
Non-IP traffic (for example AppleTalk, IPX, BPDUs, and MPLS) can be configured to go through using an EtherType access list.
Note The transparent mode ASA does not pass CDP packets packets, or any packets that do not have a valid EtherType greater than or equal to 0x600. An exception is made for BPDUs, which are supported.
Passing Traffic For Routed-Mode Features
For features that are not directly supported on the transparent firewall, you can allow traffic to pass through so that upstream and downstream routers can support the functionality. For example, by using an extended access list, you can allow DHCP traffic (instead of the unsupported DHCP relay feature) or multicast tra ffic such as that created by IP/TV. You can also establish routing protocol adjacencies through a transparent firewall; you can allow OSPF, RIP, EIGRP, or BGP traffic through based on an extended access list. Likewise, protocols like HSRP or VRRP can pass through the ASA.
BPDU Handling
To prevent loops using the Spanning Tree Protocol, BPDUs are passed by default. To block BPDUs, you need to configure an EtherType access list to deny them. If you are using failover, you might want to block BPDUs to prevent the switch port from going into a blocking state when the topology changes. See the “Transparent Firewall Mode Requirements” section for more information.
MAC Address vs. Route Lookups
When the ASA runs in transparent mode, the outgoing interface of a packet is determined by performing a MAC address lookup instead of a route lookup.
Route lookups, however, are necessary for the following traffic types:
- Traffic originating on the ASA—For example, if your syslog server is located on a remote network, you must use a static route so the ASA can reach that subnet.
- Traffic that is at least one hop away from the ASA with NAT enabled—The ASA needs to perform a route lookup to find the next hop gateway; you need to add a static route on the ASA for the real host address.
- Voice over IP (VoIP) and DNS traffic with inspection enabled, and the endpoint is at least one hop away from the ASA—For example, if you use the transparent firewall between a CCM and an H.323 gateway, and there is a router between the transparent firewall and the H.323 gateway, then you need to add a static route on the ASA for the H. 323 gateway for successful call completion. If you enable NAT for the inspected traffic, a static route is required to determine the egress interface for the real host address that is embedded in the packet. Affected applications include:
ARP Inspection
By default, all ARP packets are allowed through the ASA. You can control the flow of ARP packets by enabling ARP inspection.
When you enable ARP inspection, the ASA compares the MAC address, IP address, and source interface in all ARP packets to static entries in the ARP table, and takes the following actions:
- If the IP address, MAC address, and source interface match an ARP entry, the packet is passed through.
- If there is a mismatch between the MAC address, the IP address, or the interface, then the ASA drops the packet.
- If the ARP packet does not match any entries in the static ARP table, then you can set the ASA to either forward the packet out all interfaces (flood), or to drop the packet.
Note The dedicated management interface, if present, never floods packets even if this parameter is set to flood.
ARP inspection prevents malicious users from impersonating other hosts or routers (known as ARP spoofing). ARP spoofing can enable a “ man-in-the-middle” attack. For example, a host sends an ARP request to the gateway router; the gateway router responds with the gateway router MAC address. The attacker, however, sends another ARP response to the host with the attacker MAC address instead of the router MAC address. The attacker can now intercept all the host traffic before forwarding it on to the router.
ARP inspection ensures that an attacker cannot send an ARP response with the attacker MAC address, so long as the correct MAC address and the associated IP address are in the static ARP table.
MAC Address Table
The ASA learns and builds a MAC address table in a similar way as a normal bridge or switch: when a device sends a packet through the ASA, the ASA adds the MAC address to its table. The table associates the MAC address with the source interface so that the ASA knows to send any packets addressed to the device out the correct interface.
The ASA 5505 includes a built-in switch; the switch MAC address table maintains the MAC address-to-switch port mapping for traffic within each VLAN. This section only discusses the bridge MAC address table , which maintains the MAC address-to-VLAN interface mapping for traffic that passes between VLANs.
Because the ASA is a firewall, if the destination MAC address of a packet is not in the table, the ASA does not flood the original packet on all interfaces as a normal bridge does. Instead, it generates the following packets for directly connected devices or for remote devices:
- Packets for directly connected devices—The ASA generates an ARP request for the destination IP address, so that the ASA can learn which interface receives the ARP response.
- Packets for remote devices—The ASA generates a ping to the destination IP address so that the ASA can learn which interface receives the ping reply.
The original packet is dropped.