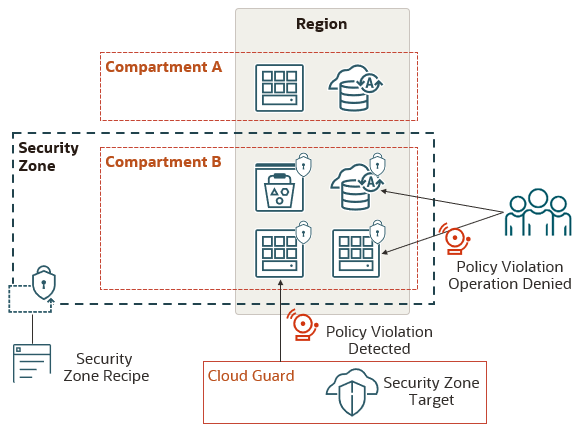
Security Zones let you be confident that your resources in Oracle Cloud Infrastructure , including Compute , Networking , Object Storage , Block Volume and Database resources, comply with your security policies.
A security zone is associated with one or more compartments and a security zone recipe. When you create and update resources in a security zone, Oracle Cloud Infrastructure validates these operations against the list of policies that are defined in the security zone recipe. If any security zone policy is violated, then the operation is denied. By default, a compartment and any subcompartments are in the same security zone, but you can also create a different security zone for a subcompartment.
For example, a security zone policy forbids the creation of public buckets in Object Storage. If you try to create a public bucket in a security zone that has this policy, or if you try to modify an existing storage bucket and make it public, you receive an error message. Similarly, you can't move an existing resource to a compartment in a security zone unless the existing resource meets all policies in the security zone.
Your tenancy has a predefined recipe named Maximum Security Recipe , which includes a number of curated security zone policies. Oracle manages this recipe and you can't modify it. You can, however, create your own recipes that meet your specific security requirements.
You must enable Oracle Cloud Guard before you create Security Zones . Cloud Guard helps you detect policy violations in existing resources that were created before the security zone.
Tip
Watch a video introduction to the service.
Understand key concepts and components related to Security Zones .
The following diagram provides a high-level overview of Security Zones .

Security zone An association between a compartment (and zero or more subcompartments) and a security zone recipe. Resource operations in a security zone are validated against all policies in the recipe. A security zone includes a compartment and all of its subcompartments, unless you explicitly remove a subcompartment from the security zone, or create a separate zone for the subcompartment. A compartment cannot be associated with more than one security zone. Security zone recipe A collection of security zone policies that Oracle Cloud Infrastructure enforces on security zones that use the recipe. Security zone policy A security requirement for resources in a security zone. If a security zone enables a policy, then any action that attempts to violate that policy is denied. Security zone target ( Cloud Guard ) A compartment in which Cloud Guard periodically checks resources for security zone policy violations. A target includes all subcompartments unless you create a separate target for the subcompartment. A target is associated with one or more detector recipes. Each detector recipe defines a list of potential security problems.
A security zone policy differs from an IAM policy in the following ways:
In general, security zone policies align with the following core security principles.
Understand the relationships between compartments, security zones, recipes, and targets.
After you create a security zone for a compartment, it automatically prevents operations, such as creating or modifying resources, that violate the security zone's policies. However, existing resources that were created before the security zone might also violate policies. Security Zones integrates with Cloud Guard to identify policy violations in existing resources.
Cloud Guard is an Oracle Cloud Infrastructure service that provides a central dashboard to monitor all of your cloud resources for security weaknesses in configuration, metrics, and logs. When it detects a problem, it can suggest, assist, or take corrective actions, based on your Cloud Guard configuration.
Here are some key Cloud Guard concepts:
Detector recipe Defines the types of cloud resources and security problems that you want Cloud Guard to monitor. Cloud Guard provides some default Oracle-managed detector recipes, and you can also create custom recipes. Target A compartment that you want Cloud Guard to monitor, and is associated with a Cloud Guard recipe. A target can be associated with multiple detector recipes, but only one of each type (configuration, activity, and so on). Security zone target A type of Cloud Guard target that is also associated with a security zone. The target monitors resources in the compartment for security zone policy violations.
The following diagram illustrates the Cloud Guard configuration for a new security zone:
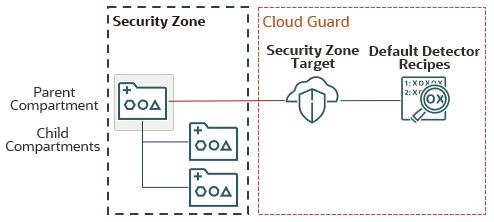
When you create a security zone for a subcompartment whose parent compartment is already in a security zone, Cloud Guard performs the following tasks:
No changes are made to the existing Cloud Guard target for the parent compartment.
The following diagram illustrates the Cloud Guard configuration for a new security zone in a subcompartment:
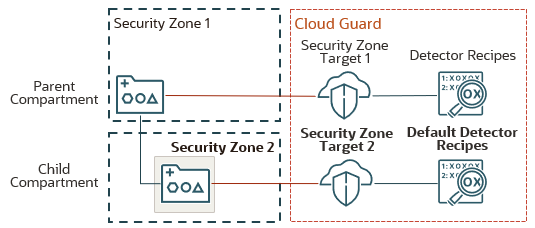 security zone and the child compartment is in a different security zone. Each compartment is associated with a different security zone target in Cloud Guard. The security zone target for the child compartment is associated with default detector recipes." />
security zone and the child compartment is in a different security zone. Each compartment is associated with a different security zone target in Cloud Guard. The security zone target for the child compartment is associated with default detector recipes." />
A single compartment can't be in multiple security zones, and also can't be in multiple Cloud Guard targets.
To learn more about Cloud Guard , see Cloud Guard Concepts.
You can access Security Zones using the Console (a browser-based interface), REST APIs, the Command Line Interface (CLI), or SDKs.
Instructions for the Console, API, and CLI are included in topics throughout this guide. For a list of available SDKs, see Software Development Kits and Command Line Interface.
Note
The Security Zones APIs are available from the Cloud Guard endpoints.
To access the Console, you must use a supported browser. To go to the Console sign-in page, open the navigation menu at the top of this page and click Infrastructure Console. You will be prompted to enter your cloud tenant, your user name, and your password.
Each service in Oracle Cloud Infrastructure integrates with IAM for authentication and authorization, for all interfaces (the Console, SDK or CLI, and REST API).
An administrator in your organization needs to set up groups, compartments , and policies that control which users can access which services, which resources, and the type of access. For example, policies control who can create users, create and manage a VCN (virtual cloud network) , launch instances, and create buckets .
In addition to creating IAM policies, follow these other security best practices for Security Zones .
When you sign up for Oracle Cloud Infrastructure , a set of service limits is configured for your tenancy. These limits restrict the total number of Security Zones resources that you can create.
See Service Limits for instructions on requesting a limit increase.
Security zone resources, like most types of resources in Oracle Cloud Infrastructure , have a unique, Oracle-assigned identifier called an Oracle Cloud ID (OCID).
For information about the OCID format and other ways to identify your resources, see Resource Identifiers.
Security Zones integrates with other monitoring services in Oracle Cloud Infrastructure .
To get started, create a security zone for an existing compartment using either an Oracle-managed or a custom recipe, and then check for any policy violations.